Client Profile
-
Industry: Mid-market company (undisclosed)
-
Environment: Microsoft 365 with Defender integrations
-
Deployment Status: First evaluation mode (no active containment or automated chat verification)
-
Security Stack: ShieldWatch integrated with M365 environment within 15 minutes
The Challenge
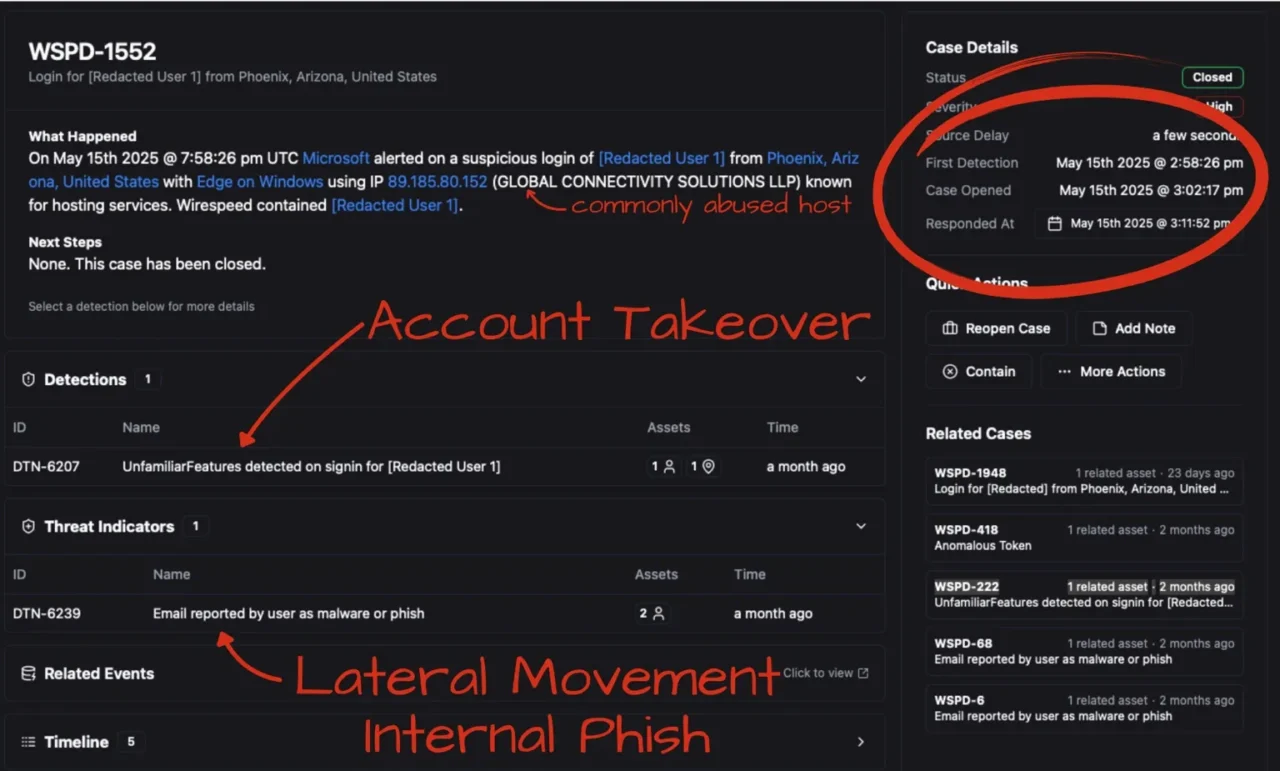
A newly onboarded prospect started his first evaluation of ShieldWatch’s XDR platform. Within minutes of integrating their Microsoft 365 stack, ShieldWatch ingested 90 days of historical telemetry and began establishing behavioral baselines.
Shortly after integration, a suspicious identity alert was triggered for one of the organization’s users. In most environments, such alerts are overlooked or buried in log files—especially during trial periods. But not with ShieldWatch.
Threat Timeline
-
Minute 0: Suspicious login from unfamiliar ASN and IP, using a common user-agent
-
+2 minutes: Detection ingested via Microsoft Defender
-
+2 seconds: ShieldWatch delivers a fast verdict (confirmed hostile)
-
+2 minutes: ShieldWatch escalates to customer’s technical team
-
+14 minutes: Account is manually disabled and all sessions terminated
All this occurred without automatic containment turned on.
The Attack
An external attacker gained unauthorized access to a user account using stolen credentials. While the access was limited, the attacker immediately attempted lateral movement by sending internal phishing emails—an increasingly common technique used to bypass perimeter defenses and trick employees with seemingly legitimate internal messages.
Example:
-
Phishing Email: A fake invoice from “Larry’s Lumber” was sent to another employee.
-
Goal: Achieve secondary compromise to escalate privileges or commit BEC (Business Email Compromise).
Fortunately, the recipient was vigilant and reported the suspicious email.
ShieldWatch Response
Despite ChatOps and Auto-Containment being disabled, ShieldWatch:
-
Correlated the rogue login with the internal phishing attempt
-
Enriched all related indicators automatically
-
Linked both events into a unified case without any human intervention
-
Escalated the threat to the IT team with full context and timeline
-
Enabled the client’s manual containment within minutes
All data and indicators were stored in ShieldWatch’s high-performance datalake for instant query and retrospective analysis—without extra ingestion fees.