The Threat
A targeted phishing campaign attempted to exploit Adversary-in-the-Middle (AiTM) tactics by redirecting users to a fake login portal that captured valid MFA session tokens. These session tokens bypass traditional MFA checks and give attackers full authenticated access.
What Happened:
-
All three targeted employees clicked the phishing link.
-
Two of them entered their credentials into the fake site.
-
Session tokens were instantly harvested and could be used by the attacker to impersonate the users.
Detection & Analysis
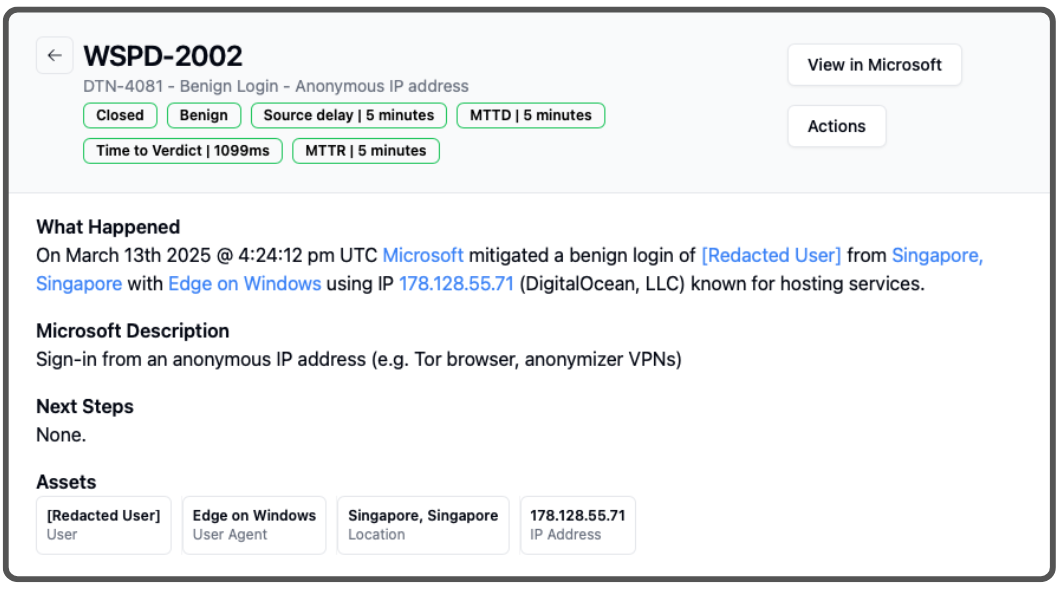
ShieldWatch instantly grouped related detections into two primary cases, each consisting of several alerts. One early detection was flagged as “benign” by Microsoft, claiming it was “mitigated” with MFA. However, ShieldWatch recognized this as an MFA bypass attempt using a reverse proxy, thanks to threat intel enrichment and behavioral analysis.
Key Details:
-
ShieldWatch identified and enriched the event with known indicators of MFA phishing infrastructure.
-
The login appeared to originate from Singapore, but both users were confirmed to be physically in the U.S..
-
ChatOps was activated to notify the users via email and request confirmation of the login activity.
-
Both users replied: “NO, that was not me.”
Timeline of Events
|
Time |
Action |
|---|---|
|
T+0 |
Phishing email received & clicked by 3 employees |
|
T+5m |
ShieldWatch triages and correlates detection patterns |
|
T+6m |
Threat intelligence confirms MFA reverse proxy attack |
|
T+7m |
ChatOps initiated to notify affected users |
|
T+17m & T+27m |
Manual containment triggered for both compromised accounts |
Response & Containment
Although automatic containment was not enabled, ShieldWatch escalated the event in real-time to the designated security administrator. Upon review, the admin confirmed the threat and used the “Contain” feature to:
-
Isolate endpoints via EDR
-
Disable user accounts in Microsoft Entra & Active Directory
-
Terminate all active sessions, including those captured by the attacker
-
Log the entire response flow in ShieldWatch’s case timeline for auditability
Total attacker access:
-
27 minutes for the first victim
-
17 minutes for the second
Data Analysis via ShieldWatch’s Data Lake
Using ShieldWatch’s integrated data lake (powered by ClickHouse), analysts were able to:
-
Instantly locate the first DNS query to the attacker’s domain
-
Trace all relevant user, host, IP, and domain activity within the threat window
-
Correlate cross-platform data (Cisco Umbrella, Microsoft Entra, EDR tools) via vendor-neutral OCSF fields
This holistic view enabled security teams to validate that no data was exfiltrated and confirmed that all malicious interactions were contained within a short time frame.
Results
|
Metric |
Outcome |
|---|---|
|
Users Affected |
3 (2 compromised) |
|
Time to First Detection |
Minutes |
|
Time to Containment |
17–27 minutes |
|
Material Impact |
None |
|
Automation Mode |
ChatOps + Manual Containment |
|
Attack Type |
MFA Reverse Proxy (AiTM) |
|
Tools Used |
ShieldWatch, Cisco Umbrella, Microsoft Entra, AD |
Lessons Learned
✅ Session tokens must be treated as credentials
✅ ChatOps reduces dwell time and involves users immediately
✅ MFA alone is not enough—AiTM phishing attacks are on the rise
✅ Threat enrichment matters: vendor verdicts are not always reliable
✅ Customer-controlled automation builds trust without sacrificing speed
✅ Data lake visibility enables root cause and impact analysis instantly
Bottom Line
ShieldWatch once again proved that speed, visibility, and automation—when paired with smart escalation workflows—can stop a breach before it becomes a headline. With 100% transparency, cross-tool correlation, and client-controlled containment, the platform delivered a win for the good guys.
Want to Know if Your MFA Is Truly Protecting You?
Schedule a breach simulation or security audit with ShieldWatch to uncover hidden risks in your authentication systems.