How to Conduct Cybersecurity Risk Assessments: Methods, Frameworks, and Tools for Practical Risk Management
A cybersecurity risk assessment systematically identifies, analyzes, and ranks threats to an organization’s information assets so leaders can make targeted decisions that lower exposure and strengthen resilience. This guide explains why rigorous assessments matter now—an accelerating threat landscape, tighter regulations, and pressure to align security spend with business outcomes—and what you’ll walk away with: practical methodologies, framework mappings, recommended tools, and a step-by-step implementation plan.
You’ll see how qualitative, quantitative, and hybrid approaches differ, how NIST, ISO 27001, CMMC 2.0 and SOC 2 map to assessment activities, and which telemetry and automation tools improve speed and accuracy. We also include enterprise-ready checklists and 2025 trends, like AI-driven detection and continuous monitoring, plus operational examples of managed detection and response that show how automation plus a human-led SOC accelerates containment and compliance reporting.
What Are the Key Cybersecurity Risk Assessment Methodologies?
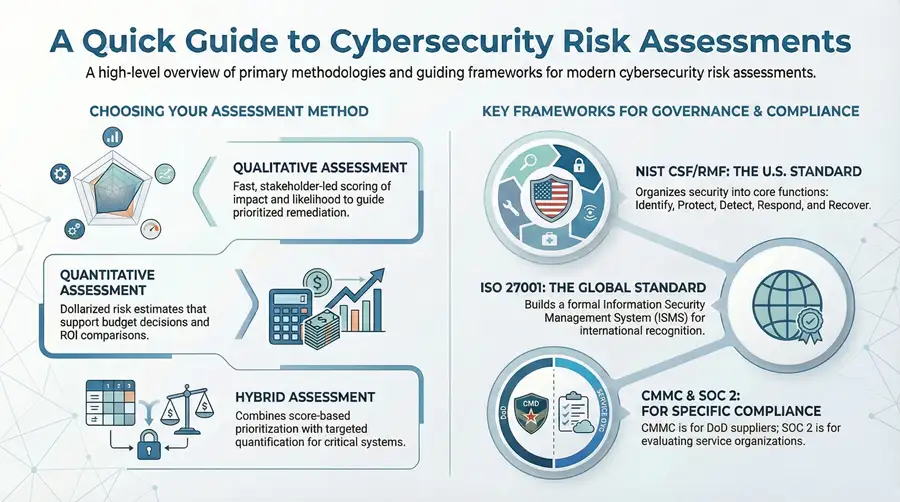
A risk assessment methodology defines how an organization catalogs assets, estimates threat likelihood, measures impact, and prioritizes remediation to reduce residual risk. Approaches trade off speed for precision: qualitative methods enable fast prioritization through stakeholder input, quantitative techniques translate exposure into financial terms for investment decisions, and hybrid models combine both to balance practicality with executive reporting. The right choice depends on business objectives, data availability, regulatory drivers, and the maturity of asset inventories and telemetry. The comparison below helps teams pick the best style for their context and shows when each method adds value.
Different methodologies fit different contexts and maturity levels:
- Qualitative Assessment: Fast, stakeholder-led scoring of impact and likelihood to guide prioritized remediation.
- Quantitative Assessment (FAIR-style): Dollarized risk estimates that support budget decisions and ROI comparisons.
- Hybrid Assessment: Score-based prioritization with targeted quantification for critical systems.
That quick list clarifies selection. Next, we compare specific named approaches for easy reference.
This table compares common methodologies and when to apply them.
This comparison helps practitioners choose a methodology and set expectations for deliverables. Next we dive into practical how-to guidance for qualitative and quantitative techniques.
How Do Qualitative Risk Assessments Identify and Prioritize Threats?
Qualitative assessments use structured scoring to rate impact and likelihood and produce a risk matrix that directs remediation without heavy modeling. Teams establish consistent impact scales (for example, negligible to catastrophic) and likelihood tiers (rare to almost certain) so subject-matter experts and business owners can agree on scores. A typical workflow includes compiling an asset inventory, cataloging threats, assessing control effectiveness, and running stakeholder workshops to validate scores and decision rules. For example, assessing a third-party vendor starts with mapping the vendor’s data access, rating compromise likelihood against controls, and assigning business impact values tied to contract and reputational risk. Best practice is to document scoring rationales and revisit qualitative ratings when telemetry or incident data change.
Qualitative methods are valuable when speed and cross-functional alignment matter, though they may lack the financial precision executives often want. Moving from qualitative prioritization to measurable remediation requires clear acceptance criteria and a regular re-evaluation cadence.
What Are Quantitative Risk Assessment Techniques and Their Benefits?
Quantitative assessments convert exposure into measurable values—frequently financial—using methods like FAIR, statistical loss models, and probabilistic scenario analysis to support investment decisions. FAIR frames risk as a function of probable frequency and probable magnitude of loss, requiring inputs such as asset value, threat capability, vulnerability rates, and control effectiveness; those inputs are modeled to produce expected loss frequency and probable loss magnitude. The outcome is a dollarized risk metric that enables cost-benefit analysis and ROI-driven prioritization. For example, modeling a likely breach of a critical application can estimate annualized loss exposure and let decision-makers compare the cost of patching, segmentation, or insurance in financial terms.
Quantitative approaches demand higher-quality data and disciplined modeling but produce clear, executive-friendly outputs. Pairing dollarized results with narrative scenarios helps stakeholders understand the risks and increases the chance of funded remediation.
Which Cyber Risk Management Frameworks Guide Effective Assessments?
Risk management frameworks translate assessment outputs into governance, control selection, and compliance evidence so organizations can turn findings into operational change. Frameworks like NIST RMF/CSF provide clear functional taxonomies—Identify, Protect, Detect, Respond, Recover, Govern—for aligning controls and metrics. ISO 27001 embeds risk treatment planning into an ISMS and requires documented assessments as audit evidence. CMMC 2.0 defines maturity levels for DoD suppliers, and SOC 2 focuses on continuous monitoring against trust criteria for service providers. Framework choice and mapping depend on regulatory exposure, customer obligations, and the organization’s risk appetite.
Frameworks help teams structure assessment outputs into control improvements and measurable compliance evidence:
This mapping shows how assessment outputs become compliance artifacts and how tool telemetry simplifies evidence collection. Next we review the toolsets that enable those capabilities.
How Does the NIST Risk Management Framework Support Cybersecurity?
NIST RMF organizes assessment and control activities around core functions—Identify, Protect, Detect, Respond, Recover—and adds governance to align security with risk tolerance and business goals. Implementing RMF starts with an authoritative asset inventory and threat modeling under Identify, then adds controls and control testing under Protect, continuous detection under Detect, and playbooks and post-incident learning under Respond and Recover. Metrics and control owners feed governance to ensure controls persist and improve. Recent updates emphasize tying security to enterprise risk management and clearer governance, which helps CISOs align programs with board-level risk tolerance.
Using RMF produces measurable control metrics and improvement cycles and underscores the need for continuous telemetry and incident evidence to validate the Detect and Respond functions—topics we cover in the tools section.
What Roles Do ISO 27001, CMMC 2.0, and SOC 2 Play in Compliance?
ISO 27001 delivers an international ISMS framework where risk assessments justify control selection—suitable for organizations pursuing broad global recognition. CMMC 2.0 targets Department of Defense contractors and maps practices to maturity levels, making it critical for suppliers handling controlled unclassified information. SOC 2 evaluates service organizations across trust criteria—security, availability, confidentiality, processing integrity, and privacy—and expects continuous monitoring and audit evidence. The right standard depends on customer requirements and regulatory exposure; many organizations map controls across frameworks to reduce duplication and streamline audits.
Below is a concise comparison to clarify applicability and evidence requirements for assessment and audit preparation.
What Tools and Solutions Enhance Cybersecurity Risk Assessments?
Tools provide the telemetry, correlation, and automation that turn static risk registers into living, evidence-driven programs. XDR platforms unify endpoint, network, cloud, and identity telemetry to deliver contextual detection signals. SIEMs centralize logs for forensic analysis; SOAR platforms automate playbooks and drive repeatable response. Vulnerability scanners and threat intelligence platforms supply prioritization inputs for vulnerability management and scenario modeling. Together, these tools reduce uncertainty in likelihood estimates and speed verification of control effectiveness—improving both qualitative scoring and quantitative models.
The table below summarizes core tool roles and the typical outputs that support assessment workflows.
This matrix shows how tools feed assessment inputs and produce measurable outputs. Next, we map a platform’s capabilities to assessment needs as a practical example.
How Does ShieldWatch XDR Integrate AI and Automation for Risk Management?
ShieldWatch XDR brings together endpoint, network, cloud, and identity telemetry and layers in AI Agent Hyperautomation plus pre-built SOAR workflows. Unified telemetry closes visibility gaps and yields more accurate likelihood and impact estimates, while AI-driven verdicting and automation speed containment—lowering probable loss in quantitative models. ShieldWatch’s 150+ pre-built SOAR playbooks standardize repeatable responses and create audit trails for control effectiveness, and its AI-Agent Collaboration with a 24/7 SOC adds human validation where models need context. The platform is designed to support SOC 2, HIPAA, ISO 27001, and CMMC 2.0 evidence collection by correlating incidents to controls and documenting remediation activity.
Using a unified XDR like ShieldWatch improves assessment precision and operational response. The following section covers the managed SOC models that commonly pair with such platforms.
What Are the Benefits of Managed SOC and Automated Incident Response?
Managed SOC services provide continuous human-led monitoring, proactive threat hunting, and rapid triage that close blind spots and speed alert validation, while SOAR automation cuts manual toil and shortens containment windows. Common benefits include faster mean time to detect and contain, consistent investigative workflows, and documented remediation actions that serve as compliance evidence. A hybrid human-plus-automation model scales for mid-market and enterprise organizations by combining 24/7 analyst oversight with automated verdicting and containment. When choosing between in-house and managed models, weigh internal skillsets, budget, and the need for continuous coverage versus on-demand support.
Combined, managed SOC and automation support continuous risk monitoring and make assessment outputs actionable by ensuring controls are tested and remediations are executed.
How Can Enterprises Implement an Effective Cybersecurity Risk Assessment Program?
An effective program turns methodology and framework choices into repeatable phases: scope and governance, asset inventory, threat and vulnerability analysis, risk analysis and prioritization, remediation planning and execution, and continuous monitoring with reporting. Governance assigns roles—CISO owns program oversight, IT/security handle technical execution, business owners validate impact, and MSP/managed SOCs provide telemetry and incident response. Defined KPIs and reporting cadences give executives concise summaries while technical dashboards show remediation backlogs and SLA-tracked tasks. Automation and managed services accelerate each phase by augmenting discovery, correlating telemetry, and executing remediation playbooks tied to the risk register.
Below is a concise, board-ready checklist to use as a starting point.
- Identify: Define scope, map data flows, and establish an authoritative asset inventory.
- Assess: Ingest telemetry, run vulnerability scans, and perform threat modeling.
- Prioritize: Score risk using qualitative, quantitative, or hybrid methods.
- Remediate: Build a prioritized remediation backlog and execute controls.
- Monitor: Maintain continuous telemetry, validate control effectiveness, and report on risk posture.
This five-step checklist outlines a clear implementation path; the next section lists essential deliverables and operational templates for each phase.
What Are the Essential Steps to Conduct a Comprehensive Risk Assessment?
Start with scoping and an authoritative asset inventory that identifies high-value assets and data flows and assigns ownership. Next, run threat modeling and vulnerability scans to build a threat catalog and vulnerability register—these feed your risk matrix or quantitative models. Score risk to produce a prioritized risk register and translate findings into a remediation backlog with owners and SLAs. Deliverables should include the risk register, remediation plan, and an executive risk dashboard; capture acceptance criteria and residual risk sign-offs. Integrating automation and managed services at this stage reduces manual discovery and speeds verification of remediation effectiveness.
These steps create documented outputs for compliance and governance and transition naturally into continuous monitoring and reporting practices.
How Does Continuous Monitoring and Reporting Improve Risk Management?
Continuous monitoring converts periodic snapshots into a live risk posture by streaming telemetry to detection engines, keeping vulnerability data current, and updating risk scores as conditions evolve. Alert-to-insight pipelines ensure incidents update the risk register and trigger re-scoring, enabling faster decisions about compensating controls or expedited remediation. Recommended KPIs include mean time to detect, mean time to contain, percent of high-risk items remediated within SLA, and residual risk trends. Automated reporting templates—executive heatmaps for leadership and playbook execution logs for analysts—deliver the right level of detail to each audience. This continuous approach lowers dwell time and generates audit-ready evidence for compliance frameworks.
By closing the loop between detection, assessment, and remediation, continuous monitoring keeps risk assessment current and actionable rather than static.
What Are the Latest Trends and Best Practices in Cyber Risk Management for 2025?
In 2025, three trends shape effective programs: broader adoption of AI-driven detection and automation, expansion of continuous monitoring and risk-as-a-service models, and more multi-framework mapping to streamline compliance. AI raises signal-to-noise ratios by automating verdicts and prioritization, but organizations must manage model validation, drift, and human-in-the-loop oversight. Risk-as-a-service and managed SOC offerings make continuous programs more accessible by bundling telemetry, analyst expertise, and compliance artifacts. Finally, multi-framework mapping reduces duplicated controls and simplifies audits by aligning control sets to NIST, ISO 27001, CMMC, and SOC 2 requirements.
Adopting these trends requires strong operational governance and a clear plan for integrating AI and managed services into assessment workflows.
How Is AI-Driven Threat Detection Transforming Enterprise Security?
AI-driven detection improves prioritization by correlating diverse telemetry and surfacing high-confidence alerts, reducing analyst fatigue and speeding containment. AI can automate verdicting and recommend remediation steps, but it needs continuous tuning, validation against ground truth, and human oversight to prevent drift and bias. Operationally, SOC workflows shift so analysts focus on validation and complex investigations while automation handles routine containment. Successful AI deployments rely on high-quality training data, tight feedback loops from analysts, and metrics that measure both model performance and business risk reduction.
When combined with governance and human validation, AI reduces time-to-contain and raises the fidelity of risk assessments.
Why Is Proactive Risk Management Critical Amid Increasing Cyber Threats?
Proactive risk management moves organizations from reacting to incidents toward anticipatory practices—threat hunting, continuous assessment, and resilience planning—that shrink dwell time and lower business impact. Proactive programs prioritize early detection, attack-surface reduction, and rehearsed response plans, which drive measurable improvements in detection and containment metrics. Practical steps include establishing a continuous-monitoring baseline, running red-team or tabletop exercises, and investing in playbook automation to lock in lessons learned. For many teams, partnering with managed detection and response providers that combine AI automation with a 24/7 SOC delivers scalable proactive capabilities that would be costly to build internally.
When evaluating operational models, look for platforms and services that combine unified telemetry, automated workflows, and human validation. ShieldWatch’s XDR—blending AI Agent Hyperautomation, extensive SOAR playbooks, and AI-Agent Collaboration with a 24/7 SOC—illustrates how to operationalize proactive risk management while producing compliance-ready evidence for SOC 2, HIPAA, ISO 27001, and CMMC 2.0. Teams aiming to reduce time-to-contain and sustain continuous assessment often find that pairing an XDR platform with managed SOC services accelerates remediation and improves audit readiness.
Next steps: map your highest-value assets to a selected methodology, pilot unified telemetry ingestion, and evaluate a managed XDR model that pairs automation with human-led operations to operationalize continuous, proactive risk management.
Frequently Asked Questions
What is the difference between qualitative and quantitative risk assessments?
Qualitative assessments rely on expert judgment and stakeholder input, using scoring systems to prioritize risks quickly. Quantitative assessments use numerical data and statistical methods to assign financial values to risk, enabling informed investment decisions. Qualitative approaches are faster and more flexible; quantitative methods deliver precision and are better suited for executive-level budget discussions.
How can organizations ensure compliance with multiple cybersecurity frameworks?
Use a multi-framework mapping approach: align overlapping controls across frameworks—NIST, ISO 27001, SOC 2, etc.—to minimize duplication and streamline evidence collection. Maintain a unified control register, map each control to framework requirements, and automate evidence capture where possible. Ongoing training and governance ensure the mappings stay current as frameworks evolve.
What role does continuous monitoring play in risk management?
Continuous monitoring turns periodic assessments into a live view of risk by streaming telemetry, keeping vulnerability data fresh, and updating risk scores as conditions change. It enables faster remediation, reduces dwell time, and produces audit-ready evidence of control effectiveness—critical for both security and compliance.
What are the key components of an effective cybersecurity risk assessment program?
Core components include clear governance, an authoritative asset inventory, thorough threat and vulnerability analysis, repeatable risk-prioritization methods, and a remediation process. Continuous monitoring, KPIs, role-based responsibilities, and automation tools round out the program to ensure it adapts to evolving threats and compliance requirements.
How can AI enhance cybersecurity risk assessments?
AI speeds analysis, improves threat detection, and surfaces predictive insights by correlating large volumes of telemetry. It helps prioritize risks, automates routine tasks like vulnerability triage, and frees analysts to focus on complex investigations. Effective AI use depends on quality data, validation workflows, and human oversight to avoid drift and bias.
What are the benefits of using managed SOC services for risk management?
Managed SOCs deliver 24/7 monitoring, expert threat hunting, and rapid incident response without the overhead of a full in-house team. They provide continuous oversight, consistent investigative processes, and documented remediation activity that supports compliance. For many organizations, managed SOCs offer a cost-effective way to scale proactive security capabilities.
Conclusion
Well-run cybersecurity risk assessments help organizations identify and prioritize vulnerabilities, enabling informed decisions that improve security posture. By choosing the right methodologies and mapping outputs to established frameworks, teams can align risk management with regulatory and business needs. Continuous monitoring and modern tooling make assessments actionable and audit-ready. Start improving your program by mapping core assets to a methodology, piloting unified telemetry, and evaluating managed XDR options that combine automation with human-led operations.




https://shorturl.fm/y1fzI