Malware analysis is the structured work of identifying, dissecting, and interpreting malicious software so teams can detect, contain, and remediate attacks more effectively. Today’s enterprises face smarter, faster campaigns that monetize data theft, extortion, and persistent access—driving up incident costs and operational disruption. This article walks through malware analysis methods and practical prevention steps, explains how Extended Detection and Response (XDR) and managed SOC services strengthen defenses, and maps controls against common threats like ransomware and fileless attacks.
You’ll find clear definitions of key malware classes, an overview of static, dynamic, and behavioral techniques, and guidance on automating containment with SOAR and agentic AI. We also show how enterprise XDR and managed SOCs fuse telemetry, threat intelligence, and playbooks to cut false positives and speed recovery.
By the end, both technical teams and executives will have actionable context on tactical analysis and the strategic platform choices that drive resilient malware prevention.
What Are the Key Types and Attack Vectors of Modern Malware?
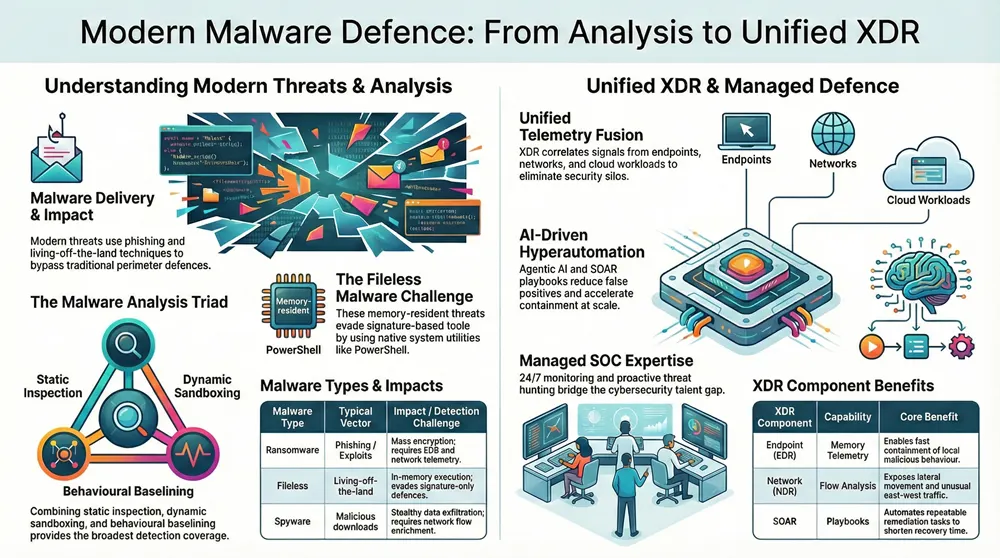
Malware is any software created to perform unauthorized actions on systems. Modern variants differ by delivery method, persistence mechanisms, and operational impact. Adversaries use vectors such as phishing, supply-chain compromise, exploit kits, malicious macros, and living-off-the-land techniques—and each vector shifts the signals defenders must collect and the response priorities. Knowing these types and vectors helps you focus telemetry, shape threat-hunting hypotheses, and improve prevention. The table below gives a compact reference to guide technical and executive prioritization around detection complexity and likely business impact.
The table below compares representative malware classes, their primary vectors, and operational impacts to assist prioritization.
This side-by-side view explains why different malware classes require distinct telemetry and tailored response playbooks—and why detection becomes harder when attackers reuse native tools or hide exfiltration paths.
How Do Ransomware, Spyware, Trojans, and Fileless Malware Differ?
Ransomware typically encrypts or steals data to extort victims and often moves laterally using compromised credentials. Spyware quietly collects information over long periods, making network flow and telemetry enrichment essential for discovery. Trojans masquerade as legitimate software to install backdoors or credential-stealing modules, which improves the signal value of file-integrity and binary-provenance checks. Fileless malware avoids writing files to disk, running instead in memory via scripting or native tools—so behavioral analysis and endpoint telemetry correlation become critical.
Each class also leads to different remediation actions: rapid containment and recovery for ransomware, forensic data-loss assessment for spyware, credential resets and app hardening for Trojans, and memory forensics plus policy enforcement for fileless threats. These distinctions inform which detection layers—endpoint, network, identity—should be emphasized in an XDR deployment.
What Are Common Malware Attack Vectors and Their Impacts?
Frequent vectors include phishing emails with malicious attachments or links, compromised public-facing services, third-party software supply-chain breaches, document macros, and removable media. Phishing remains the dominant initial access method and often triggers identity and email telemetry alerts. Supply-chain attacks can bypass perimeter controls by introducing trusted but compromised binaries. Exploit-driven intrusions often create noisy network indicators and exploit-specific signatures, while removable media can bridge air-gapped systems in sensitive environments. Each vector produces distinct telemetry—email headers, process creation events, network connections, and authentication logs—that an XDR platform must correlate to deliver timely detection.
Mapping vectors to telemetry guides incident response playbooks and triage priorities, helping analysts choose the right containment steps—revoking credentials after phishing or isolating hosts after exploit detection, for example. Effective prevention pairs user-awareness and patch management with telemetry fusion to shorten dwell time and limit operational impact.
How Does Extended Detection and Response Enhance Malware Prevention?
Extended Detection and Response (XDR) is a detection-and-response architecture that unifies telemetry from endpoints, network, cloud workloads, and identity systems so teams get correlated detections and automated responses. By aggregating diverse signals, XDR cuts alert noise, enables cross-domain hunting, and shortens MTTD/MTTR. It depends on telemetry normalization, correlation rules, and analytics—often enriched by threat intelligence—to surface high-confidence incidents for analysts and automation. The table below maps core XDR components to their capabilities and the concrete benefits teams can expect when planning platform integration.
When these XDR components work together, they create detection synergies and give operations the tools to track and disrupt multi-stage malware campaigns.
What Are the Core Capabilities of ShieldWatch XDR for Unified Threat Detection?
ShieldWatch XDR combines autonomous analytics with SOC workflows to streamline alert triage and response. The platform pairs agentic AI for incident scoring and enrichment with extensive, pre-built SOAR playbooks for hyper-automation, plus rapid deployment and retroactive log visibility for retrospective hunting. AI-enabled triage reduces analyst time on low-fidelity alerts by prioritizing and enriching incidents; hyper-automation enforces consistent containment across environments. Fast onboarding and 90-day historical analysis support root-cause investigations and hunting without long wait times.
Those capabilities translate into concrete malware-prevention outcomes: quicker detection of living-off-the-land activity, automated containment for ransomware propagation, and reduced operational load for internal teams. This mapping helps security leaders see how XDR features convert into fewer false positives and shorter incident lifecycles.
How Does AI-Driven Automation Improve Malware Detection and Response?
AI-driven automation scores alerts, enriches context, and suggests or executes containment actions to triage threats faster and cut analyst workload. Enrichment pulls user identity, asset criticality, and event history so analysts view a prioritized, contextual incident. Integrated with SOAR playbooks, AI can trigger containment actions—like isolating a host or revoking sessions—while preserving human approval for high-risk moves. Analyst feedback loops continuously refine AI scoring, boosting precision and lowering false positives.
This mix of agentic AI and human oversight accelerates containment and enables repeatable, scalable responses across enterprise environments. Next, we detail the core malware analysis techniques that feed these detection and automation layers.
What Advanced Malware Analysis Techniques Are Used to Identify Threats?
Advanced analysis uses static, dynamic, and behavioral approaches to expose malicious intent and observable effects—each with distinct strengths and limits. Static analysis examines code and binaries for signatures, indicators, and suspicious constructs without running the sample; it’s fast and scalable but vulnerable to obfuscation. Dynamic analysis executes samples in instrumented sandboxes to trace runtime behavior—network calls, file-system changes, and process activity—though sophisticated samples can detect sandbox environments. Behavioral analysis builds baselines from real-world telemetry and flags anomalies across endpoints and network flows, making it powerful against fileless and zero-day threats. Combining these techniques in automated pipelines and correlating results with telemetry yields the broadest detection coverage.
Feeding static, dynamic, and behavioral outputs into threat intelligence and XDR correlation enables precise verdicting and faster containment. The table below clarifies when each technique is most effective and their trade-offs.
Use this mapping to prioritize techniques based on threat complexity and the telemetry you can collect.
How Does Static and Dynamic Malware Analysis Work in Enterprise Environments?
In enterprise pipelines, static analysis typically performs automated unpacking, metadata extraction, and heuristic scoring to flag known indicators and route candidates to deeper inspection. Dynamic analysis runs suspect binaries in instrumented sandboxes to capture process trees, file-system changes, and network behavior; outcomes feed IOC lists and behavioral signatures. The balance is scalability versus fidelity: static checks cut noise, sandboxing provides behavioral proof, and XDR integration ensures sandbox findings correlate with live telemetry across the estate.
Operational challenges include sandbox evasion, the compute cost of large-scale dynamic analysis, and the need to tie sandbox outputs to endpoint and network logs. Effective pipelines push high-confidence behaviors into SOAR playbooks for automated containment and surface ambiguous cases for analyst review.
What Role Does Behavioral Analysis Play in Detecting Zero-Day Threats?
Behavioral analysis builds baselines of normal user, host, and network activity and flags deviations that indicate unknown or zero-day threats—especially when attackers rely on living-off-the-land techniques. By correlating process activity, abnormal parent-child relationships, unusual network connections, and identity events, behavioral systems reveal sequences static signatures miss. For example, a one-off PowerShell invocation that performs an encoded download followed by odd outbound connections can signal a fileless compromise even without a signature. XDR platforms amplify behavioral detection by combining endpoint, network, and cloud signals into higher-confidence anomalies that justify automated containment or analyst investigation.
Continuous tuning and analyst feedback reduce false positives and improve baseline accuracy, making behavioral analysis a core capability for uncovering previously unseen campaigns.
How Do Managed Security Operations Centers Support Continuous Malware Defense?
Managed Security Operations Centers (managed SOCs) provide continuous monitoring, expert triage, and proactive hunting to complement in-house teams and maintain steady defense coverage. A managed SOC integrates with an organization’s XDR platform to ingest correlated detections, run playbooks, and escalate verified incidents to internal responders. For organizations with limited resources, managed SOCs deliver senior analyst expertise and hunting capabilities without the overhead of recruiting and retaining specialized staff. The table below highlights core managed SOC offerings and the operational value they deliver.
These managed services create a continuous defense posture that complements platform automation and raises overall security maturity.
What Are the Benefits of 24/7 Threat Monitoring and Expert Incident Response?
Round-the-clock monitoring ensures alerts are triaged quickly, containment steps happen without delay, and escalating incidents get immediate expert attention—reducing mean time to detect and respond. Experienced responders apply playbook-driven containment, collect forensic evidence, and guide remediation to minimize downtime and preserve data for post-incident reviews. Continuous monitoring also supports proactive hunting and retrospective investigations using retained logs, helping organizations find long-running intrusions that initially slipped through. These operational advantages translate into measurable gains: fewer analyst hours per incident and lower business impact from breaches.
Partnering with a managed SOC extends an organization’s security coverage and expertise while freeing internal teams to focus on strategic improvements rather than constant operations.
How Does Managed SOC Address the Cybersecurity Talent Shortage?
Managed SOCs help organizations overcome talent gaps by supplying staffed analyst shifts, senior hunting capability, and playbook development without the burden of hiring and training specialized staff. This model reduces recruitment and retention costs and provides consistent expertise through joint exercises and reporting. For teams that can’t build a full SOC, a managed service offers immediate access to threat hunting, coordinated incident response, and continuous tuning of detection rules. Over time, the managed relationship can upskill internal stakeholders and embed mature operational practices.
That approach lets constrained internal resources concentrate on strategic priorities while the managed SOC handles 24/7 operational duties, preserving institutional knowledge and strengthening resilience.
How Does Automation and SOAR Enable Rapid Incident Response and Containment?
Security Orchestration, Automation, and Response (SOAR) codifies playbooks to automate repetitive tasks—enrichment, remediation, and notifications—while keeping humans in control for sensitive decisions. SOAR workflows speed containment by chaining actions like isolating endpoints, blocking IPs, and revoking credentials into a single runbook. When integrated with XDR telemetry, context-aware triggers launch the right playbooks based on confidence scores and asset criticality. Common SOAR steps and their impact on containment speed and consistency include:
- Enrichment: Collect contextual data (user, asset, history) to inform decisions.
- Containment: Isolate affected hosts or block malicious network indicators.
- Remediation: Execute cleanup tasks such as credential resets and patching.
- Post-Incident: Open tickets, update IOC lists, and run lessons-learned processes.
These automated sequences cut manual toil, enforce consistent responses, and shorten incident lifecycles so analysts can focus on complex investigations requiring human judgment.
What Are SOAR Workflows and Their Impact on Malware Threat Containment?
SOAR workflows are repeatable playbooks that orchestrate detection-to-response activities across tools and teams: they enrich alerts, carry out containment actions, and record remediation steps for audit and compliance. Encoding best practices into automated routines ensures fast, consistent containment even during alert surges. Examples include automatic host isolation on confirmed ransomware indicators and coordinated credential revocation after phishing compromises. These workflows reduce routine analyst work, lower response variability across shifts, and improve auditability.
Deploying SOAR workflows delivers measurable benefits: faster playbook execution, fewer manual steps per incident, and clearer evidence trails for compliance.
How Does AI Agent Hyperautomation Facilitate Automated Incident Response?
AI Agent Hyperautomation leverages agentic AI to recommend or execute playbook steps, simulate analyst decisions for low-risk alerts, and learn from human feedback to improve future actions. Agents can triage by scoring and enriching alerts, then trigger predefined SOAR playbooks or present prioritized options for analyst approval. The feedback loop—where analyst verdicts and remediation outcomes feed model updates—sharpens recommendations and reduces repetitive false-positive handling. Human-in-the-loop controls preserve governance while delivering speed and scale.
Combining agentic decision-making with controlled execution raises operational throughput and helps organizations respond to complex malware campaigns more quickly and consistently.
How Does ShieldWatch Support Compliance and Risk Management in Malware Prevention?
ShieldWatch aligns XDR and managed SOC capabilities with compliance objectives by providing continuous monitoring, evidence collection, and reporting that support audit readiness across common frameworks. The platform’s telemetry retention, automated playbooks, and reporting artifacts demonstrate control operation and help meet regulatory requirements. The table below maps referenced frameworks to ShieldWatch XDR features that support relevant control objectives.
These mappings illustrate how continuous detection and standardized response improve compliance readiness and lower audit risk.
Which Regulatory Frameworks Does ShieldWatch XDR Align With for Security Compliance?
ShieldWatch XDR supports frameworks commonly referenced in platform guidance—SOC 2, HIPAA, CMMC 2.0, and ISO 27001. Centralized logging and continuous monitoring help meet evidence requirements by producing timely alerts, retained event histories, and automated reporting artifacts for audits. Pre-built SOAR workflows enforce consistent, policy-driven responses while historical visibility enables retroactive evidence collection during assessments. Integrating these capabilities into a compliance program reduces the manual effort of gathering evidence and documenting recurring incidents.
Mapping platform features to control objectives simplifies audit preparation and makes security posture demonstrable to assessors.
How Does Compliance Readiness Reduce Malware-Related Risks and Breaches?
Compliance readiness lowers risk by ensuring controls—timely patching, least-privilege access, continuous monitoring, and tested incident response—are implemented, documented, and exercised. Continuous detection shortens dwell time by surfacing anomalies earlier, while automated playbooks ensure containment steps run reliably during incidents, reducing impact. Combined with historical visibility, automation speeds post-incident investigation and corrective actions, limiting repeat exploit paths. Organizations that stay audit-ready are better positioned to find and fix control gaps before adversaries exploit them.
This proactive posture aligns security operations with regulatory expectations and reduces both operational and compliance exposure.
Why Choose ShieldWatch for Malware Analysis and Prevention
ShieldWatch stands out by combining autonomous AI with SOC operations, extensive pre-built SOAR workflows for hyper-automation, rapid deployment with retroactive 90-day log visibility, and built-in support for compliance frameworks such as SOC 2, HIPAA, CMMC 2.0, and ISO 27001. Together, these capabilities unify detection, response, and compliance in a single XDR platform that lowers false positives and accelerates investigations. Organizations choose ShieldWatch to reduce alert fatigue, use agentic AI for prioritized triage and action, and adopt standardized playbooks that scale across distributed environments.
- Reduced False Positives: Unified telemetry and AI triage cut noise so analysts focus on real threats.
- Faster Incident Lifecycle: Pre-built SOAR workflows and automated containment shorten MTTR.
- Compliance Support: Automated evidence collection and reporting streamline audits and control validation.
Choosing ShieldWatch helps security teams convert detection into reliable, auditable responses while keeping human oversight and operational control. Request a demo or evaluation to see how these capabilities map to your risk profile and operational needs.
Frequently Asked Questions
What is the difference between malware analysis and malware prevention?
Malware analysis is the investigative process of examining malicious code to understand how it behaves and what it targets—information used to build detection and remediation. Malware prevention focuses on blocking malware from entering and executing in the first place—through firewalls, endpoint controls, user training, and hardening. Analysis informs prevention by revealing tactics, techniques, and procedures adversaries use, while prevention is the proactive layer that reduces attack surface and exposure.
How can organizations improve their malware detection capabilities?
Improve detection by adopting an XDR approach that centralizes telemetry from endpoints, network, cloud, and identity systems, and by feeding that data into behavioral analysis and threat intelligence. Regularly update intelligence feeds, tune detection rules, run table-top exercises, and train staff to spot social engineering. A layered security strategy—combined with continuous hunting and automated playbooks—ensures multiple detection points and faster response.
What role does user education play in malware prevention?
User education is vital: well-trained employees reduce the likelihood of successful phishing and social-engineering attacks. Ongoing awareness programs, simulated phishing, and role-specific training reinforce safe behaviors and make users an effective first line of defense alongside technical controls.
What are the challenges in detecting fileless malware?
Fileless malware runs in memory and leverages legitimate system tools, so it leaves little or no disk footprint and can bypass signature-based defenses. Effective detection depends on behavioral telemetry, process-parent relationships, command-line inspection, and correlation with network and identity signals. Continuous monitoring and endpoint detection (EDR) are essential to spot these stealthy activities.
How does threat intelligence enhance malware analysis?
Threat intelligence adds context—actor patterns, IOCs, TTPs—that helps prioritize alerts and shape detection rules and playbooks. Integrating intelligence into analysis pipelines speeds identification of campaigns and improves the accuracy of automated containment and hunting efforts.
What is the significance of automated incident response in malware containment?
Automated response reduces the time between detection and containment, minimizing damage. By codifying proven actions into SOAR playbooks—such as isolating hosts or blocking indicators—organizations shorten MTTD/MTTR, lower manual workload, and let analysts concentrate on complex investigations rather than repetitive tasks.
How can organizations ensure compliance while managing malware risks?
Align security controls with relevant frameworks (SOC 2, HIPAA, ISO 27001, CMMC 2.0), maintain centralized logging and retention, and use automated playbooks and reporting to produce auditable evidence. Embedding compliance into operational routines reduces manual evidence collection and helps demonstrate that controls work as intended during assessments.
Conclusion- Secure Your Enterprise with ShieldWatch
Effective malware analysis and prevention combine rigorous technical methods—static, dynamic, and behavioral analysis—with unified telemetry and automated response at the platform level. XDR architectures and managed SOC services provide continuous detection, prioritized triage, and repeatable containment that lower dwell time and operational impact from modern threats. ShieldWatch pairs agentic AI, hyper-automation, fast deployment, and compliance-centered features to help organizations detect, contain, and recover from malware faster and with fewer false positives. For enterprises aiming to strengthen prevention and response, a unified XDR platform backed by managed SOC expertise is a practical path to resilient, auditable security operations.
Conclusion
Bringing advanced malware analysis techniques together with a unified XDR platform improves an organization’s ability to detect, respond to, and recover from threats. Continuous monitoring, automated incident response, and compliance readiness reduce operational impact and dwell time from malware attacks. ShieldWatch empowers security teams to streamline operations, cut false positives, and strengthen resilience. Reach out to explore how ShieldWatch can modernize your malware prevention strategy.




Start sharing, start earning—become our affiliate today!
Monetize your traffic with our affiliate program—sign up now!